This article provides a comprehensive overview of blockchain technology, explaining its inner workings and exploring its diverse applications in today’s world.

What is Blockchain Technology?
Blockchain technology is a distributed database system that records and stores digital asset data in blocks in a transparent and immutable way. These blocks are linked together through cryptographic hash functions and arranged chronologically to form a chain.
Blockchain technology is also known as Distributed Ledger Technology (DLT) because it is not controlled by any central authority or intermediary. This decentralization makes blockchain secure and resistant to tampering, as any changes to the data require consensus from the majority of the network.

When Was Blockchain Invented? A Brief History
While the concept of blockchain technology was first introduced in the early 1990s by researchers Stuart Haber and W. Scott Stornetta, it wasn’t until late 2008 that the technology gained widespread recognition. This was thanks to Satoshi Nakamoto‘s whitepaper introducing Bitcoin, a peer-to-peer (P2P) electronic cash system, which clearly outlined the workings of blockchain technology.
Key milestones in blockchain history:
- Early 1990s: Stuart Haber and W. Scott Stornetta propose a system for timestamping digital documents using cryptographic techniques, laying the foundation for blockchain.
- Late 2008: Satoshi Nakamoto publishes the Bitcoin whitepaper, outlining a decentralized digital currency system based on blockchain technology.
- January 3, 2009: The Bitcoin blockchain is born with the mining of the first block (genesis block) by Satoshi Nakamoto.
- January 12, 2009: The first Bitcoin transaction takes place, with Satoshi sending 10 BTC to Hal Finney.
Since then, blockchain technology has evolved rapidly, with numerous applications beyond cryptocurrencies. Today, blockchain is being used in various industries, including supply chain management, healthcare, and voting systems.

Satoshi Nakamoto’s Bitcoin whitepaper introduced the world to Bitcoin, a peer-to-peer electronic cash system built on blockchain technology. This innovation aimed to address the limitations of traditional transactions while eliminating the double-spending problem and the need for intermediaries like banks and payment processors. metzdowd.com
What is double-spending?
Double-spending refers to the act of using the same digital currency unit to make two separate payments. Traditionally, this issue was solved by relying on trusted third parties to verify transactions. However, blockchain technology offers a groundbreaking solution that eliminates the need for such intermediaries.
How does blockchain prevent double-spending?
Blockchain achieves this by creating a decentralized and transparent ledger of all transactions. Every transaction is recorded on the blockchain and validated by a network of computers. Once a transaction is confirmed and added to the blockchain, it becomes immutable and cannot be altered or reversed. This ensures that each unit of digital currency can only be spent once.
Read more: History of Blockchain
Blockchain Structure: A Chain of Blocks
Blockchain, true to its name, is structured as a chain of blocks. Here’s a simple breakdown:
- Blocks: These are the fundamental building blocks of a blockchain. Each block contains a set of transaction data. Think of it like a page in a ledger, recording various transactions that have occurred.
- Chain: These blocks are linked together chronologically, forming a chain. Each block contains a reference to the previous block, creating a secure and tamper-proof chain of records. This chronological linking ensures that the data is organized and traceable.
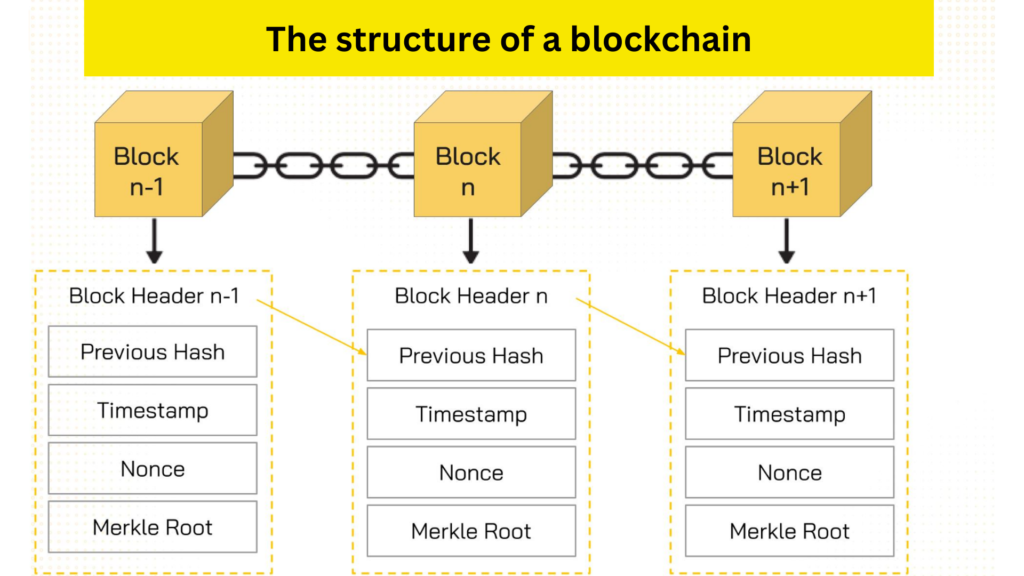
A blockchain, as the name implies, is a chain of blocks linked together. Each block plays a crucial role in maintaining the integrity and security of the entire system. Let’s delve into the components that make up a block:
1. Block Header: Think of this as the block’s identity card. It’s a unique code (a hash) that contains vital information for identifying the block within the blockchain. This includes:
- Previous Hash: A link to the previous block’s hash, ensuring that the chain remains unbroken and tamper-proof.
- Timestamp: Records the time when the block was created.
- Nonce: A random number used in the mining process to generate a unique hash for the block.
- Merkle Root: A condensed representation of all the transactions within the block, ensuring data integrity.
2. Previous Hash: This acts as a link in the chain, connecting the current block to the one before it. This chronological linking ensures that any attempt to alter a block would require changing all subsequent blocks, making it incredibly difficult to tamper with the data.
3. Timestamp: This records the precise time when the block was created, adding a temporal dimension to the blockchain.
4. Nonce: This is a critical component in the mining process. Miners compete to find a nonce that, when combined with the other block header information, results in a valid hash. This process secures the network and adds new blocks to the chain.
5. Merkle Root: This is like a digital fingerprint of all the transactions within the block. It’s derived by hashing the transactions in a specific way (using a Merkle tree) to create a single, unique hash that represents all the data in the block efficiently.
What is a Hash?
A hash is a unique code generated from any input data using a cryptographic hash function. It acts like a digital fingerprint, ensuring data integrity. Any change to the input data will result in a completely different hash.
How Does Blockchain Technology Work?
Blockchain technology operates through a series of steps that ensure secure and transparent transaction processing. Here’s a simplified breakdown of the process:
Step 1: Transaction Initiation
A user initiates a transaction request. This could involve transferring cryptocurrency, recording data, or executing a smart contract. The transaction information is then broadcast to the blockchain network, creating a record that awaits validation.
Step 2: Transaction Verification
Computers on the network, known as nodes, receive the transaction record and begin the verification process. They use consensus algorithms to ensure the transaction is valid.
Example: Let’s say a user wants to send 3 Bitcoins:
- The nodes verify if the user’s wallet actually contains 3 Bitcoins.
- If the wallet has sufficient funds, the transaction is approved.
- If the wallet has less than 3 Bitcoins (e.g., only 1 Bitcoin), the transaction is rejected.
Step 3: Block Creation
Once a transaction is verified, it’s grouped with other validated transactions and added to a “block.” This block acts like a container for storing transaction data.
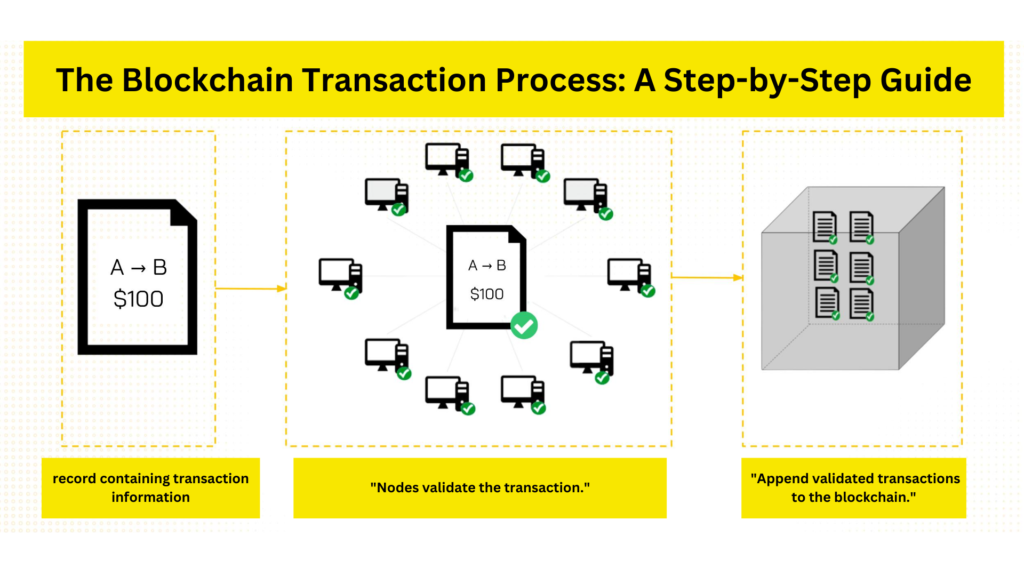
Step 4: Adding the Block to the Chain
The newly created block is added to the chain by linking its “Previous Hash” to the hash of the preceding block, thus forming a blockchain.
The very first block, having no predecessor, has a “Previous Hash” value of a string of zeros. This block is known as the genesis block.

Learn more: How to calculate transaction fees on blockchain
6 Key Characteristics of Blockchain Technology
Blockchain technology possesses unique properties that set it apart from traditional systems. These characteristics are crucial to its ability to provide secure, transparent, and efficient solutions. Here’s a breakdown of six key features:
Decentralization:Blockchain operates independently of any central authority or organization.The network is maintained by a distributed network of nodes (computers) that collectively validate transactions and maintain the ledger.This eliminates single points of failure and reduces the risk of censorship or manipulation.
Distribution:The blockchain ledger is not stored in a single location but is distributed across numerous nodes globally.This distributed nature enhances resilience and fault tolerance. If one node fails, others can continue operating, ensuring the network remains functional.
Immutability:Once data is recorded on the blockchain, it cannot be altered or deleted.This immutability is achieved through cryptographic hashing and consensus algorithms. Any attempt to modify data would require altering all subsequent blocks, which is computationally infeasible.
Security:Blockchain employs cryptography to secure information and protect against unauthorized access.Each block has a unique cryptographic hash, linked to the hash of the previous block, forming a secure chain.Any attempt to tamper with data would require changing all subsequent hashes, making it virtually impossible.
Transparency:All transaction data on a blockchain is publicly accessible and viewable by anyone.This transparency promotes accountability and trust, as all participants can audit the ledger.
Trustlessness:Blockchain operates on a trustless model, meaning participants don’t need to trust each other or a central authority.The network relies on cryptographic algorithms and consensus mechanisms to ensure validity and prevent fraud.Nodes follow predefined rules and don’t need to rely on trust to maintain the network.
Blockchain Consensus Algorithms
A blockchain consensus algorithm is a rule or mechanism that nodes follow to ensure that transactions performed on the blockchain are accurate and consistent across all nodes in the network.
If data within a block in the network is changed, it will be compared with the data in other blocks to ensure accuracy and consistency with the preceding block. If there is a discrepancy, the system will not allow that data to be written to the blockchain. This is how blockchain is designed to resist data alteration.
Example: Suppose a hacker attacks and alters the information on block number n. At that time:
The hash of block n is changed.
The system compares the hash of block n with the hash of the previous block to detect the discrepancy.
The hacker must then change the hash of the block before n. The system again detects a discrepancy in block n-1. The hacker must continue to change the hash of block n-2, and so on.
Thus, to change a transaction, the hacker must change all blocks to comply with the blockchain’s consensus mechanism.

Consensus algorithms help ensure the accuracy and transparency of a blockchain.
A consensus algorithm is an essential part of a blockchain, playing a core role in keeping blockchains decentralized and secure. Some common consensus algorithms include:
- Proof of Work (PoW): Miners use their computing power to solve mathematical problems that generate hashes. Upon solving these problems, they earn the right to validate transactions and create new blocks in the blockchain. Examples: Bitcoin, Ethereum, Litecoin, Monero…
- Proof of Stake (PoS): Users must stake (lock up) a large amount of coins/tokens to earn the right to become a node that validates transactions and creates blocks. Examples: Ethereum 2.0, Polkadot, Algorand…
- Delegated Proof of Stake (DPoS): Token holders can vote to select and delegate nodes to perform transaction verification. Examples: EOS, Tron, BitShares…
- Proof of Authority (PoA): This algorithm emphasizes the value of identity and reputation of participants rather than the value of tokens they hold. Examples: MakerDAO, VeChain…
The Evolution of Blockchain Technology
To date, blockchain technology has evolved through various stages with the emergence of different applications, including: Currency, Smart Contracts, Decentralized Applications, and Industrial use cases.
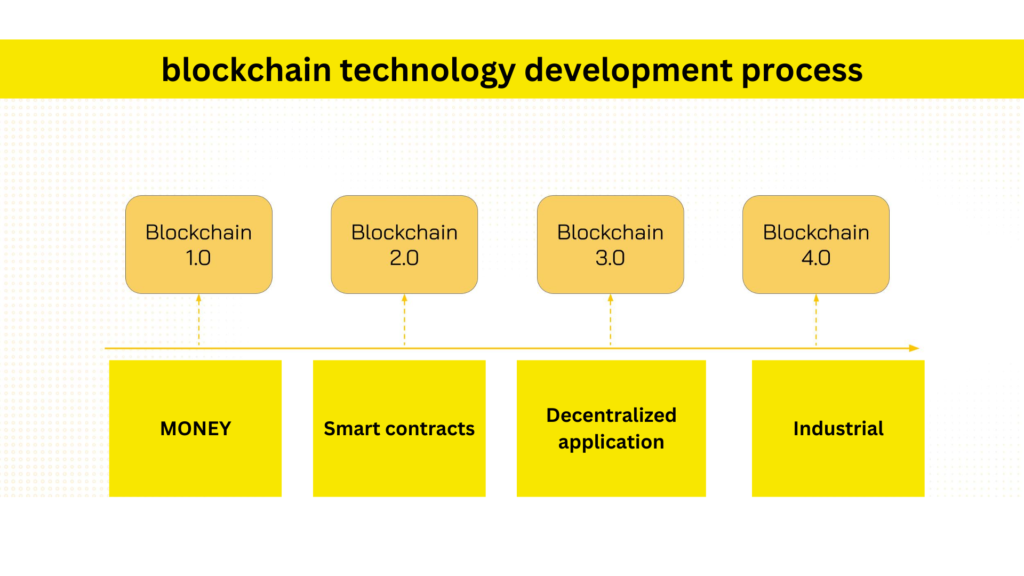
1. Blockchain 1.0: The Currency Revolution (2009 – Present)
- Bitcoin: The first and most well-known cryptocurrency, Bitcoin demonstrated the feasibility of a decentralized digital currency based on blockchain technology.
- Alternative Cryptocurrencies (Altcoins): Numerous alternative cryptocurrencies emerged, each with its own features and use cases, like Litecoin, Ripple, and many others.
2. Blockchain 2.0: The Rise of Smart Contracts (2014 – Present)
- Ethereum: The Ethereum blockchain introduced smart contracts, self-executing contracts with terms directly written into code. This opened up a world of possibilities for decentralized applications.
- Decentralized Finance (DeFi): DeFi applications emerged, offering financial services like lending, borrowing, and trading without intermediaries.
3. Blockchain 3.0: Decentralized Applications (DApps) (2017 – Present)
- Expanding Use Cases: Blockchain 3.0 focused on the development of DApps, applications that run on a decentralized network. These applications are not hosted on a single server but rather operate on a distributed network, offering increased security, censorship resistance, and data integrity.
- Examples: DApps span various sectors, including gaming, social media, supply chain management, and decentralized finance (DeFi).
4. Blockchain 4.0: Industrial Transformation (Present and Beyond)
- Integrating Blockchain into Industry: This latest iteration aims to integrate blockchain technology into various industrial processes and business operations.
- Potential Applications: Blockchain 4.0 can revolutionize supply chains, enhance data management, improve transparency and traceability in manufacturing, and streamline various business processes.
Applications of Blockchain Technology
Blockchain technology has emerged as a transformative force with applications across various sectors. Here are some of the most prominent use cases:
1. Cryptocurrencies:
- Decentralized Digital Cash: Blockchain’s first and most well-known application is in cryptocurrencies like Bitcoin and Ethereum. These digital currencies leverage blockchain’s secure and transparent nature to enable peer-to-peer transactions without intermediaries.
2. Smart Contracts:
- Self-Executing Agreements: Smart contracts are self-executing contracts with the terms of the agreement directly written into lines of code. They automate the execution of agreements, eliminating the need for intermediaries and reducing the risk of fraud.
- Increased Efficiency and Trust: Smart contracts offer increased efficiency, transparency, and trust in various processes, from supply chain management to legal agreements.
3. Supply Chain Management:
- Enhanced Traceability and Transparency: Blockchain can be used to track goods and products throughout the supply chain, from origin to delivery. This enhances transparency, improves traceability, and reduces the risk of counterfeit goods.
4. Digital Identity:
- Secure and Verifiable Identity: Blockchain can be used to create secure and verifiable digital identities, giving individuals greater control over their personal information and reducing the risk of identity theft.
5. Real Estate:
- Streamlining Property Transactions: Blockchain can streamline property transactions by creating a secure and transparent record of ownership, reducing paperwork, and minimizing the need for intermediaries.
6. Copyright and Intellectual Property:
- Protecting Creative Works: Blockchain can be used to register and protect intellectual property rights, ensuring that ownership and attribution are clearly recorded and immutable.
7. Banking and Finance:
- Increased Efficiency and Reduced Costs: Blockchain can improve efficiency and reduce costs in financial transactions by automating processes, eliminating intermediaries, and reducing the need for reconciliation.

