How can I secure my account and prevent cyberattacks? Let’s explore one of the security methods in this article.

What is 2FA?
2FA (Two-Factor Authentication) is an authentication security method for access and identity that aims to protect assets, personal information, and prevent cyberattacks. This method requires the user to provide two separate factors for login.
These two factors include:
- First factor: Is the password, this information is set and customized by the user.
- Second factor: Is the 2FA code, this information is sent by the system.
In which, the 2FA code is the OTP code used to authenticate the second factor in the 2FA process. This code is sent via SMS message, email, 2FA application (such as Google Authenticator, Authy) … when logging in or making a transaction.
In the crypto market, login information to wallets, exchanges, etc. can be easily compromised and stolen over the internet. Therefore, exchanges and wallets often require a 2FA code to enhance security and ensure the safety of users’ assets.
Why should I get a 2FA code?
In today’s digital age, when all transactions can be done over the internet, using a 2FA code for authentication is an effective way to protect users from threats targeting account login information. For example:
- Brute Force Attack: Hackers use software that helps guess passwords, private keys… by combining many different characters, and trying until it is correct to be able to access the user’s account.
- Spyware Attack: Hackers use Spyware to infiltrate devices and obtain personal information related to accounts and user passwords.
- Data Breach Attack*: Hackers use a list of usernames and passwords that have been previously leaked (through a data breach) to access other user accounts.
*Data Breach is a cyberattack that occurs when hackers gain unauthorized access to and retrieve sensitive information of an individual, a group, or a software system.
In fact, hackers can take advantage of data breaches to sell account & password pairs on the dark web, making many passwords less secure.
According to Verizon’s 2017 Data Breach Investigations Report, 81% of account hacks are related to passwords being leaked through these trades, or due to passwords being too weak (e.g. “passw0rd”) and easy to guess.
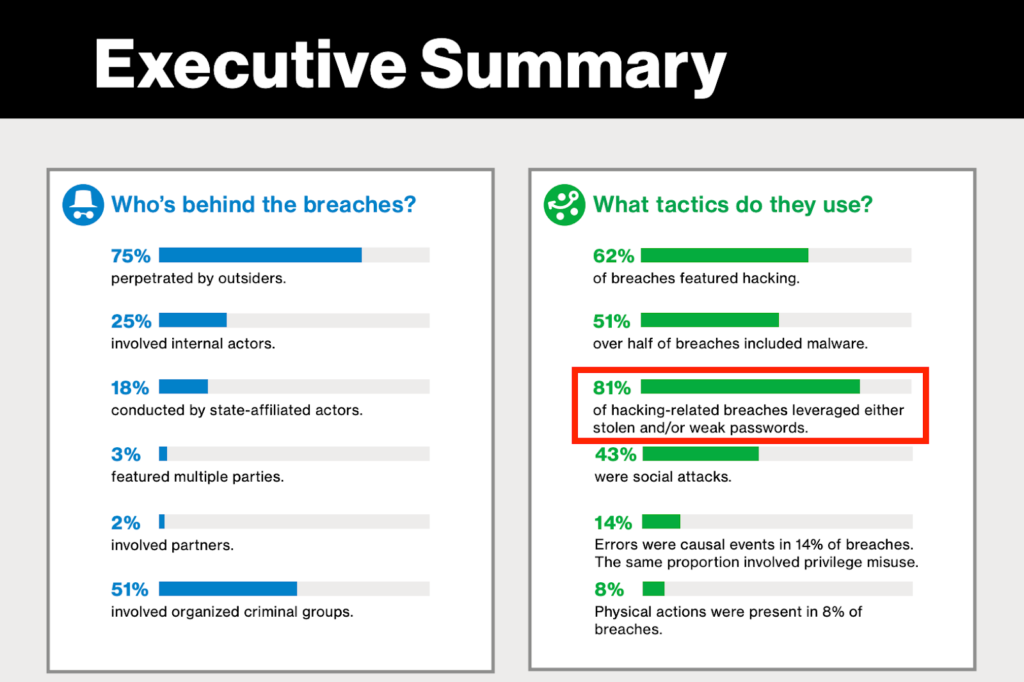
81% of hacks are related to password leaks and/or weak passwords. Source: Verizon
Especially for the crypto market, where user assets are stored via a private key, the consequences and damage caused by data breaches are even worse. The LastPass lawsuit is a prime example of this.
In August 2022, LastPass (a password management service) announced that their system had been hacked in a data breach, leaking all user information provided on LastPass.
Then, on January 3, 2023, user John Doe filed a lawsuit against LastPass alleging that: LastPass’s data breach resulted in the theft of Bitcoin in his wallet.
Previously, John used LastPass Vault and followed LastPass’s security recommendations to store the private key information of the Bitcoin wallet (with a total value of 53,000 USD). Following the announcement of the leak, John quickly deleted the information on the Vault. However, John claims that hackers used the leaked private key data and stole all the Bitcoin in his wallet.
It can be seen that password management services still do not guarantee complete security for user information and assets. Therefore, requiring 2FA authentication for each transaction is necessary and more important than ever for crypto users.
How 2FA Works in Crypto
Once two-factor authentication has been enabled for any website, application, account, etc., the user will have to provide an additional 2FA code each time they need to:
- Log in to the account.
- Change account password.
- Make money transfer and withdrawal transactions
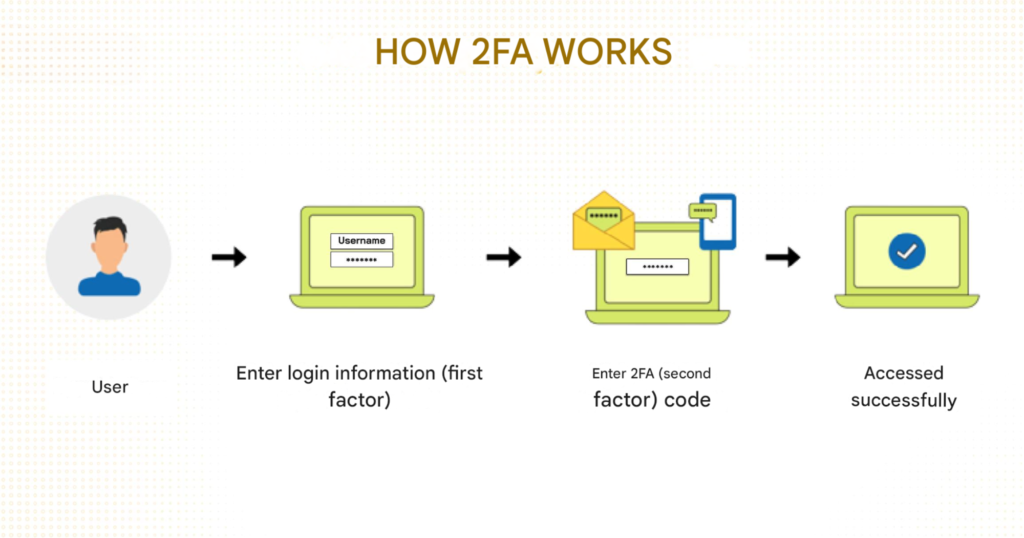
The basic 2FA authentication process will take place as follows:
Step 1. The user enters login information including username and password.
Step 2. The 2FA code will be sent to the user via SMS message, email, 2FA authentication application… to verify that the login user is the account owner.
Step 3. The user enters the 2FA code on the website, application, account… and successfully accesses it
Benefits of 2FA Code
Authentication via 2FA code brings benefits to both users and businesses or service providers such as exchanges, wallets, etc. Some benefits of 2FA include:
- Enhanced security for user accounts.
- Reduced risk of fraud and data breaches.
- Increased user trust in service providers.
- Reduced operating costs for businesses in securing user data (compared to biometric authentication methods).
Besides, the nature of the crypto market is not subject to the management of state agencies, leading to a lack of regulations and supervision of transactions, making cryptocurrencies more vulnerable to attack and theft.
Therefore, the increasing number of crypto applications (such as centralized exchanges, crypto wallets…) implementing the 2FA authentication feature shows that they are trying to implement measures to protect users’ assets. This contributes to enhancing the prestige of the market in general and products and services in particular.
2FA Authentication Methods
SMS or Voice Message
This 2FA method requires direct interaction with the user’s mobile phone.
After entering login information, the system will send a 2FA code to the registered phone number via text message or a call to read the code. The user then has to enter the OTP to gain access to the account.
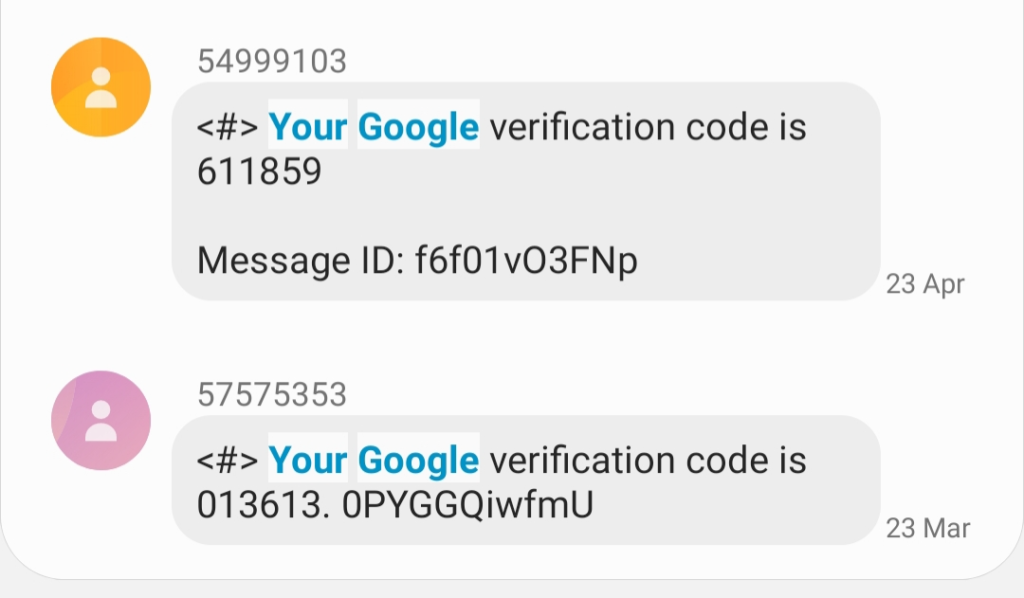
However, 2FA authentication via SMS and voice is becoming less secure. Because hackers can use sophisticated tricks called SIM Swapping* to take control of the user’s phone number, and at the same time take over the account linked to that phone number.
*SIM Swapping is a form of attack in which bad actors take advantage of vulnerabilities from the network operator, or employees of the network operator to take over the victim’s phone number.
2FA Authentication App
This is the most popular 2FA method. Users can use the 2FA authentication application on their phone or computer to generate a 2FA code via the Timed One-Time Passwords (TOTP) algorithm.
This algorithm allows the application to generate OTP codes continuously after each certain period of time (30 or 60 seconds), with the note that each code is only valid during that time.

Some popular 2FA authentication applications:
- Google Authenticator (GA): A popular 2FA authentication application developed by Google.
- Authy: A 2FA authentication application with the ability to sync across multiple devices and back up codes, preventing users from losing access to their accounts in case of phone loss.
- Microsoft Authenticator: A 2FA authentication application developed by Microsoft. In addition to supporting TOTP, it also has biometric authentication capabilities with fingerprint and facial recognition.
Other forms
In addition, there are a number of other forms of 2FA authentication such as:
- Push notifications: Websites and applications will send push notifications directly to users when there is an authentication request. This is a form of authentication that does not require a password, does not require entering a code, and does not require further interaction, just answer “Yes” or “No”.
- Security Key (Hardware token): The 2FA verification code is provided on a physical device such as
- Biometric authentication (Biometric 2FA): 2FA authentication method using fingerprints, facial recognition or voice. Modern mobile devices often support at least one form of biometric authentication.
How to get 2FA code
This article will quickly guide you through how to enable two-factor authentication and get 2FA codes for popular applications like Facebook, Google, Telegram.
Steps to get 2FA code on Facebook:
Step 1. Open the Facebook app, select Settings & privacy.
Step 2. Select Settings, then Security and login.
Step 3. In the Two-Factor Authentication section, select Use two-factor authentication.
Step 4. Select the security method as Authentication app.
Step 5. Enter the code string displayed on Facebook into the authentication app to link the account.
Thus, the user has successfully activated 2FA on Facebook and can get the Facebook 2FA code when there is an authentication request.
Steps to get 2FA code on Google:
Step 1. Visit the Account Settings page and sign in to your Google Account.
Step 2. In Security, under How you sign in to Google, select 2-Step Verification and Get started.
Step 3. Enter the password and captcha code received, then select Next.
Step 4. Select Continue for Google to set up phone-based verification. Then enter the phone number, select the form of receiving the code and Send.
Step 5. After you have the verification code, enter the code and click Next.
Step 6. Select Turn on to finish activating 2-layer verification.
Telegram
Steps to get 2FA code on Telegram:
Step 1. Open the Telegram application and log in to your account, select Setting.
Step 2. Select Privacy and Security, then select Two-Step Verification.
Step 3. Fill in the password and select Set Password to create a security key code for Telegram when accessing on another device.
Step 4. Fill in the key code 2 times in the Create Password and Re-enter Password boxes, then fill in the password hint and email to restore the Telegram security code, in case the user forgets that key code.
Thus, the user has successfully activated 2FA on Telegram. When logging in to Telegram on another device, the user will be asked to enter a verification code sent in the Telegram application or via SMS.
See more: Instructions for simple 2FA setup with Google Authenticator.

