Thanks to encryption, transactions, personal information and digital assets are securely protected from cyber-attacks, ensuring privacy and data integrity. Learn about data encryption in crypto through the article below.

What is data encryption?
Data encryption is a method that uses cryptographic algorithms to protect information. When encrypted, data becomes a string of unreadable characters without a “key” to decrypt it. This ensures that only authorized people can access the information.
For example, when you send a message through secure applications, that message is encrypted to prevent anyone (other than the recipient) from reading the content.
In the field of cryptocurrency, encryption is applied in many aspects, from securing cryptocurrency wallets, authenticating transactions, to protecting data on decentralized platforms.

Why is data encryption important in Crypto?
Data encryption helps protect information from unauthorized access, loss, or alteration. With the rise of cyberattacks and data breaches, encryption has become a crucial tool for ensuring the security of organizations and individuals. Applications of encryption include:
- Protecting sensitive information: Such as customer information, financial data, and medical records.
- Ensuring data integrity: Keeping data unchanged during storage or transmission.
- Securing online transactions: Ensuring that transactions are not interfered with or tampered with.
Some specific applications of data encryption:
- Crypto wallet security: The private keys of crypto wallets are encrypted to protect access. Only the key owner can make transactions.
- Digital signatures: Encryption is used to authenticate transactions, ensuring they are carried out by the rightful owner of the assets.
- Privacy transactions: Some blockchains like Monero and Zcash use encryption to hide details about transactions, protecting user privacy.
- Decentralized storage: Platforms such as Filecoin or IPFS use encryption to protect data stored on a decentralized network, ensuring that only authorized individuals can access the information.
Components of Data Encryption
Data encryption is a complex process but can be understood through the following main components:
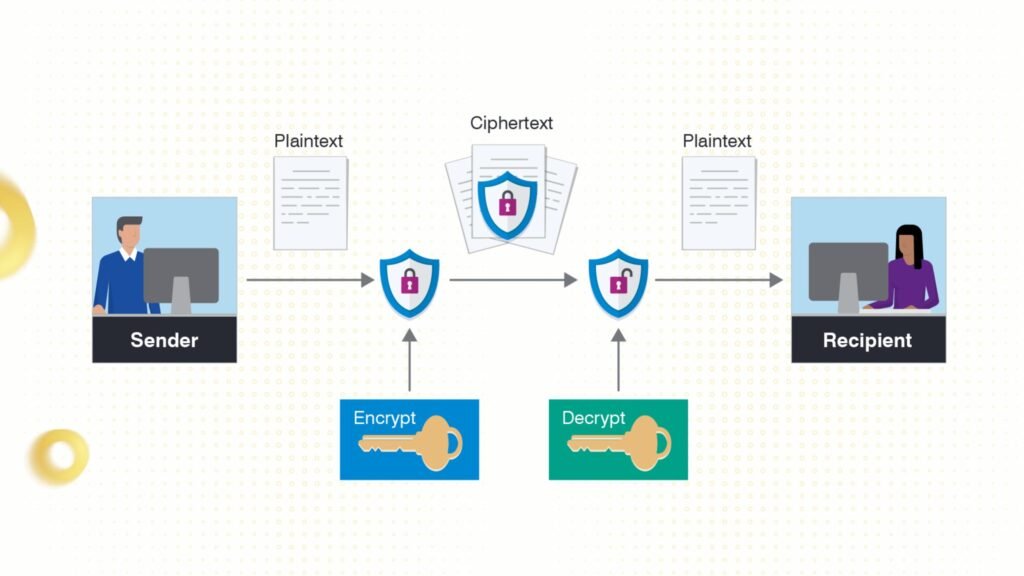
Plaintext (Raw Data)
- Plaintext is the original, understandable, and readable form of data that has not been encrypted. This can be text, images, audio files, or any other information.
- Role: Plaintext is the input of the encryption process. This data is often protected because it contains sensitive or important information.
Example: A credit card number like “1234-5678-9101-1121” is plaintext before being encrypted for secure storage or transmission.
Ciphertext (Encrypted Data)
- Ciphertext or an encrypted document is the result after data has been encrypted. It is a form of data that is unintelligible and unreadable without the proper decryption key.
- Role: Ciphertext helps protect data during storage or transmission, preventing unauthorized access.
Example: After encryption, the string “1234-5678-9101-1121” might become “XyZa@45^&Klm123”
Encryption Algorithm
- An encryption algorithm is a set of rules or mathematical procedures used to transform plaintext into ciphertext and vice versa.
- Role: The algorithm is at the heart of the encryption process, determining the security level of the data.
Examples: Common encryption algorithms include AES (Advanced Encryption Standard) for symmetric encryption and RSA for asymmetric encryption.
Encryption Key
- An encryption key is a string of characters or numbers used with an algorithm to encrypt and decrypt data.
- Role: The key is the determining factor in who has access to the encrypted data.
Types of encryption keys:
- Symmetric key: The same key is used for both encryption and decryption.
- Asymmetric key: Consists of a key pair
- Public key: Used to encrypt data.
- Private key: Used to decrypt data.
Example: When sending a secure email, the recipient will use their private key to decrypt data encrypted with their public key.
Encryption and Decryption Process
- Encryption: The process of transforming data from plaintext to ciphertext.
- Decryption: The reverse process, converting ciphertext back to plaintext using the appropriate decryption key.
Example: When you conduct an online banking transaction, your credit card data is encrypted before being sent, and only the bank’s server can decrypt it.
Data Encryption Methods in Crypto
In the field of crypto, data encryption is carried out through many advanced methods. Among them, symmetric-key encryption, asymmetric-key encryption, and cryptographic hash functions are the three most common methods.
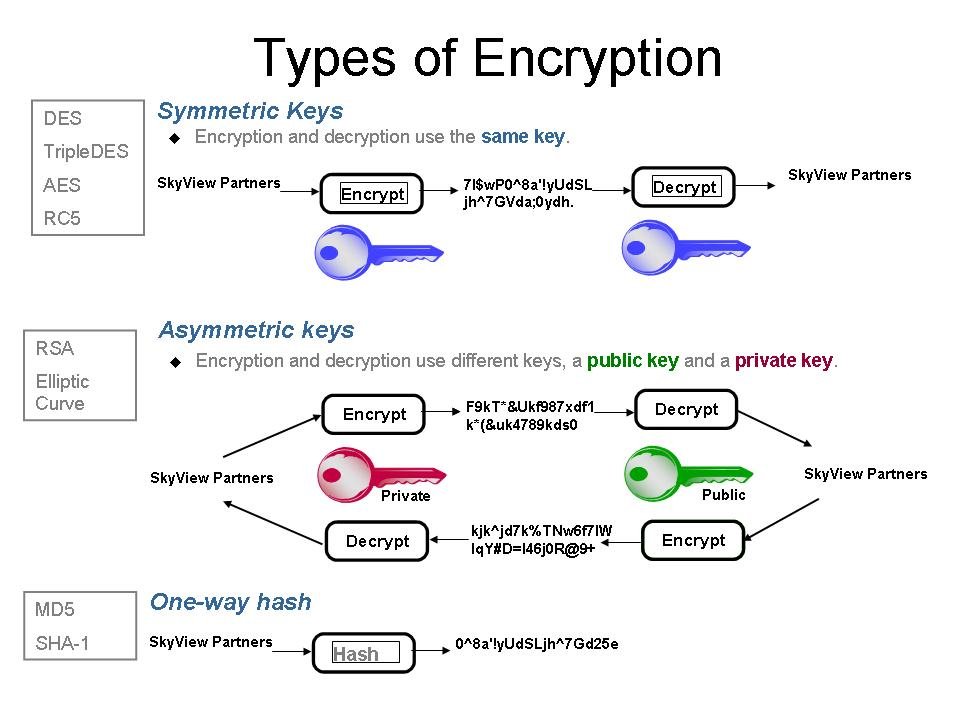
Symmetric Encryption
This method utilizes a single key for both data encryption and decryption.
- High speed, suitable for processing large volumes of data.
- Simple and efficient in applications requiring real-time processing.
Some algorithms: AES (Advanced Encryption Standard), Triple DES (3DES/TDES), Format Preserving Encryption (FPE), Blowfish…
Further reading: What is Symmetric Encryption? Understanding Symmetric Keys in Security.
Asymmetric Encryption
This method employs two distinct keys: a public key for encryption and a private key for decryption. It forms the foundation of many blockchain systems, facilitating identity verification and transaction security.
- High security as it eliminates the need to share the private key.
- Supports identity verification through digital signatures.
Some algorithms: RSA, Elliptic Curve Cryptography (ECC), Digital Signature Algorithm (DSA), Diffie-Hellman Key Exchange…
Learn more: Applications of Asymmetric Encryption in Crypto.
Cryptographic Hash Functions
This method transforms data into a unique string of values. Hash functions, such as SHA-256 used in Bitcoin, ensure that any alteration in the data is immediately detectable.
- Ensures data integrity.
- Facilitates easy detection of any data modification.
Example algorithms: SHA-256, SHA-3.
Hybrid Encryption
Hybrid encryption combines symmetric and asymmetric encryption to leverage the advantages of both methods:
- High speed of symmetric encryption.
- Enhanced security in key sharing through asymmetric encryption.
Application: SSL/TLS protocol in secure data transmission.
Homomorphic Encryption
Homomorphic encryption allows direct computations on encrypted data without decryption. The result of the computation, when decrypted, is equivalent to performing the computation on the original data.
- Protects data even during processing.
- Ideal for cloud computing and processing sensitive data in healthcare and finance.
End-to-End Encryption (E2EE)
End-to-end encryption safeguards data throughout its transmission from sender to recipient. Only the sender and recipient can decrypt the data, preventing access even by intermediary service providers.
- Commonly used in secure messaging applications like WhatsApp and Signal.
- Maximizes privacy in communication.
Risks Associated with Data Encryption
Data encryption plays a crucial role in safeguarding information and transactions within the cryptocurrency realm. However, several notable risks persist:
Loss of Encryption Keys: Private keys are the gateway to accessing and managing cryptocurrency assets. If users lose or forget these keys, they may permanently lose access to their holdings. It is estimated that approximately 20% of the 18.5 million Bitcoins are currently inaccessible, lost, or locked in dormant wallets.
Attacks on Cryptocurrency Exchanges: Cryptocurrency exchanges are frequently targeted by hackers. In November 2023, the cryptocurrency industry witnessed a series of attacks and rug pulls, resulting in losses exceeding $340 million. The three largest attacks targeted the exchanges Poloniex ($125 million), HTX ($86 million), and Kronos Research ($25 million).
Risks from Users: Users lacking security awareness can fall victim to phishing attacks or malware, leading to the disclosure of their private keys. Sharing private keys or employing insecure storage practices can also result in the loss of assets.
Mitigation Measures:
- Utilize a hardware wallet: Store private keys on a physical device to minimize the risk of hacking.
- Enable two-factor authentication (2FA): Enhance account security.
- Stay informed about security practices: Users should regularly update their knowledge of threats and protective measures.
- Choose reputable exchanges: Prioritize exchanges with robust security policies and a positive track record.
The aforementioned risks underscore the importance of raising awareness and implementing appropriate security measures when managing and transacting with cryptocurrencies.
Further reading: What are Schnorr Signatures? The benefits of Schnorr signatures in Crypto.

