In the world of cryptocurrency, ensuring the security and integrity of data is paramount. One of the core security tools that underpins these crucial aspects is the hash function.

What is a Hash Function?
A hash function is a cryptographic algorithm that takes an input of any length (a string of data such as text, numbers, or complex data) and produces a fixed-length string of characters, commonly referred to as a “hash” or “digest.”
Key Characteristics of Hash Functions:
- Consistent Input-Output: The same input will always produce the same output. This ensures that data can be reliably verified using its hash.
- One-Way Function: It’s impossible to reverse a hash to determine the original input. This protects sensitive information, like passwords, even if the hash is compromised.
- Easy Computation: Hash functions can quickly generate a hash from any input, regardless of its size. This makes them efficient for various applications.
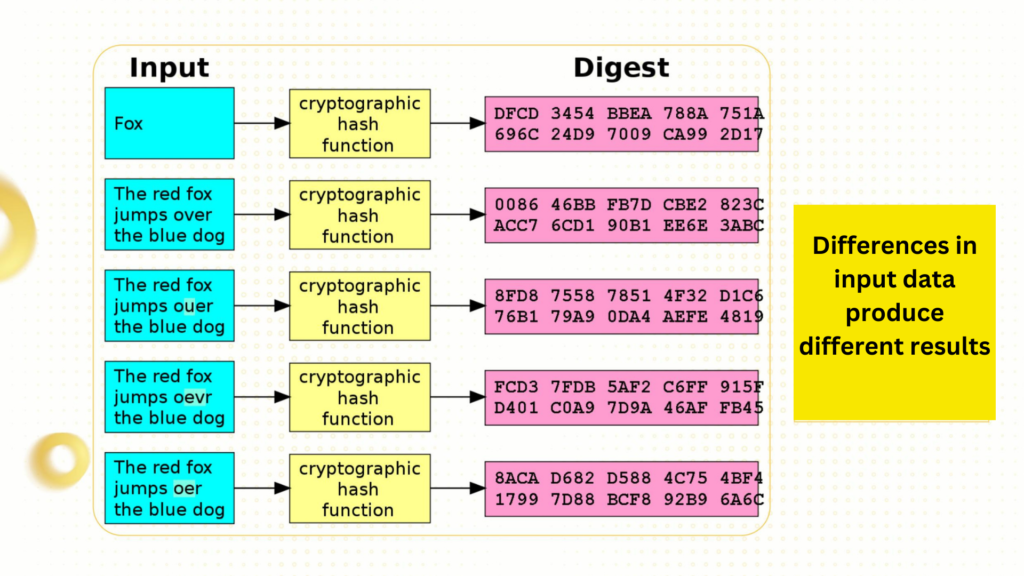
- Avalanche Effect: Even a minor change in the input data results in a completely different hash. This property, known as the “avalanche effect,” makes hash functions highly sensitive to data alterations, enhancing security.
Hash functions are used in the crypto market to protect user information, enhance transaction security, and prevent data modification.
The Vital Role of Hash Functions in Cryptography
Hash functions are more than just security tools; they are fundamental building blocks of blockchain technology and cryptocurrencies. Their unique properties enable many of the core functionalities that make blockchain secure, transparent, and reliable.
Ensuring Transaction Integrity
Hash functions play a vital role in verifying the integrity of transactions. Every transaction on a blockchain is hashed, creating a unique digital fingerprint for that transaction. This means that any alteration to the transaction, no matter how small, will result in a completely different hash. This allows the network to instantly detect any tampering and ensures that transaction data remains unchanged.
Securing the Blockchain
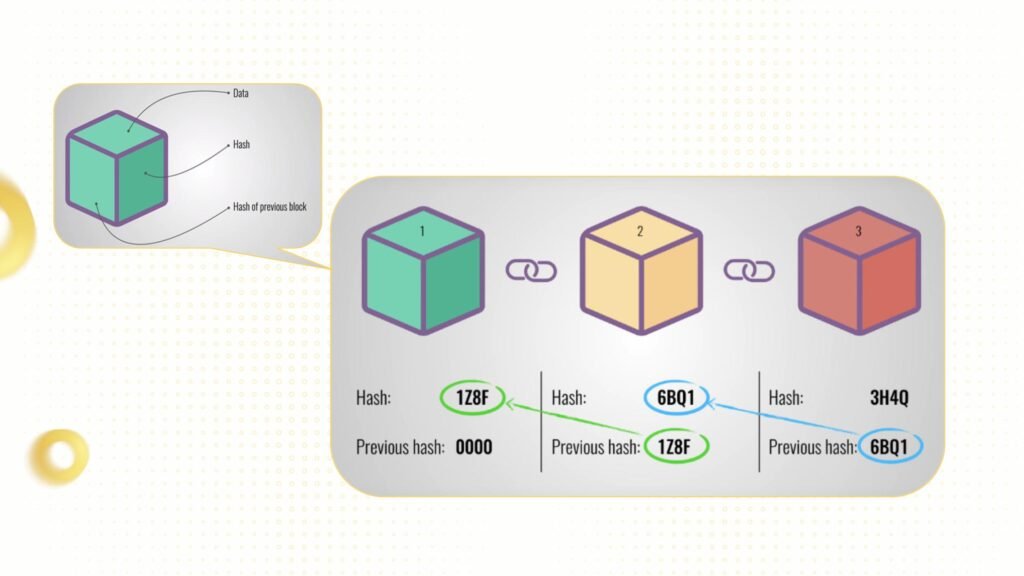
Hash functions are also crucial for securing the blocks in a blockchain. In systems like Bitcoin, each block contains a unique hash that is linked to the transactions within that block. When a new block is created, it includes the hash of the previous block, creating a chain of interconnected blocks. This structure makes it extremely difficult for malicious actors to alter any block in the chain. To change a single block, a hacker would need to change all subsequent blocks, which is computationally infeasible.
Hash function is also an important factor in the cryptocurrency mining process. Miners must solve hashing problems to find new blocks and receive rewards. This problem typically requires solving a hash string that has some special properties, making the mining process a resource-intensive task but necessary to maintain the security of the network.
Hash function also protects user personal information. When a user creates a cryptocurrency wallet, the hash function encrypts their private keys, helping to protect the wallet from unauthorized access.
Common Hash Algorithms in Crypto
In the crypto field, several prominent hash algorithms are widely used to secure transactions and data on the blockchain. These algorithms have varying levels of security and performance:
1. SHA-256 (Secure Hash Algorithm 256-bit)
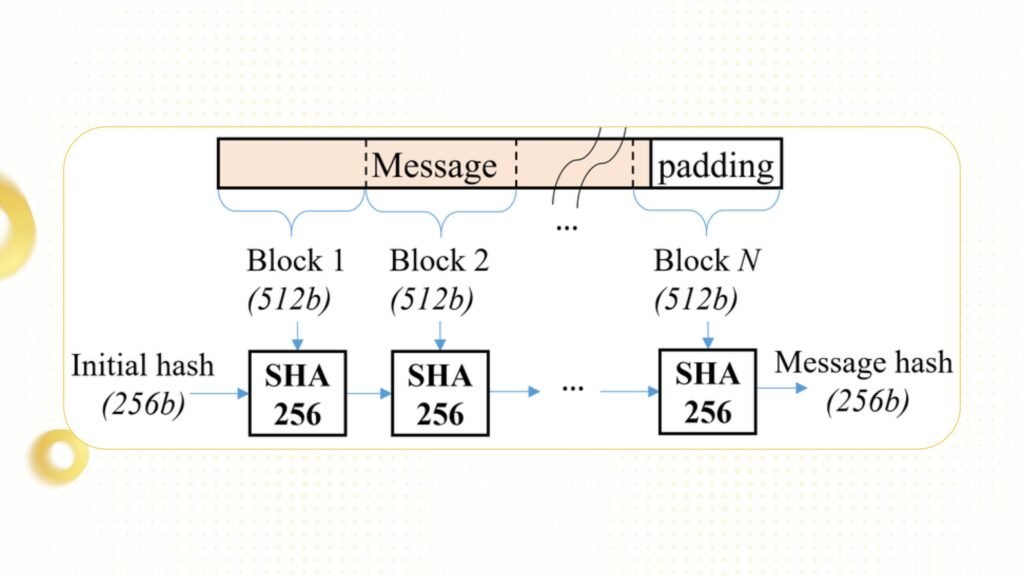
SHA-256 is the most common hash algorithm, used in Bitcoin and many other blockchains. SHA-256 generates a 256-bit string from any input data and offers high security, with approximately 2^256 possible combinations. This makes brute-force decryption of SHA-256 hash strings virtually impossible. SHA-256 also plays a crucial role in Bitcoin’s PoW mechanism, helping to prevent attacks and maintain the decentralization of the network.
2. Ethash
Ethash is the hash algorithm used in Ethereum before its transition to Ethereum 2.0 and Proof of Stake (PoS). Ethash requires a large amount of memory, which helps prevent ASIC mining and encourages the use of GPU mining. This allowed Ethereum to maintain decentralization, as ordinary users could participate in mining.
3. Scrypt
The Scrypt algorithm is used in Litecoin and several other cryptocurrencies. Scrypt is less resource-intensive than SHA-256, allowing for easier mining with CPUs or GPUs, making it a popular choice for small-scale miners who don’t need specialized mining equipment.
4. Keccak-256
Keccak-256 is the hash algorithm used by Ethereum after its transition to PoS. Keccak-256 is an improved version of SHA-3, optimizing security and performance for modern blockchain systems.
The Importance of Hash Functions in Crypto Security
Hash functions are considered a crucial element in protecting blockchain systems from attacks and ensuring data integrity. They help detect and prevent data alterations on the blockchain, as any minor change in the data will result in a completely different hash string. This helps protect the blockchain from data manipulation attacks.
Hash functions also help defend against brute-force attacks. The 256-bit length of the hash string creates a space with 2^256 possible combinations, making it virtually impossible to try all combinations to crack the code, even with supercomputers.
Learn more: What is a Brute-Force Attack?
Hash functions also help maintain the decentralization of the blockchain, allowing all participants to verify the integrity of the data without needing to trust any intermediary.
Despite their many benefits, hash functions still face some challenges and risks.
One of the biggest risks is the possibility of collisions, where two different pieces of data produce the same hash string. Although hash algorithms like SHA-256 are designed to minimize the possibility of collisions, theoretically, this risk still exists. If hackers can create a collision, they can generate fraudulent data while keeping the hash string the same.
Hash functions are also resource-intensive. In particular, in the PoW mechanism, solving hash problems requires mining devices that consume a lot of energy. According to a report by Cambridge, Bitcoin mining consumes over 120 TWh of electricity per year, creating a significant environmental impact.
Furthermore, with some blockchains transitioning to the PoS mechanism, the role of hash functions in block mining has significantly decreased. However, hash functions still play a vital role in security and data verification.
The Future of Hash Functions in the Crypto Market
In the future, hash algorithms are expected to continue evolving to meet the increasing security demands of the crypto market.
New generation hash algorithms like SHA-3 and Blake3 are being researched to improve performance and security. These are potential candidates to replace older hash algorithms when necessary, helping blockchain systems enhance security and optimize efficiency.
One of the major challenges in the future is the potential for attacks from quantum computers. Experts are researching quantum-resistant hash algorithms, as quantum computers can decrypt much faster than traditional computers. This will be a crucial development to ensure that blockchains remain secure as quantum computers become more powerful.
In recent years, NIST (the National Institute of Standards and Technology) has launched the NIST Post-Quantum Cryptography Standardization competition to select new encryption algorithms that can resist quantum computers.
NIST’s Post-Quantum Cryptography Standardization
This project aims to develop cryptography standards for the future, including hash algorithms that can resist attacks from quantum computers. NIST has selected several algorithms for the final round of the competition, including lattice-based cryptography and hash-based cryptography, which are believed to have the potential to protect blockchain from quantum attacks.
Hash Functions and Zero-Knowledge Proofs (ZKPs)
In addition, hash functions are expected to be more widely used in new security mechanisms like Zero-Knowledge Proofs (ZKPs), which allow users to prove access without revealing detailed information. This will help improve security and privacy for users.
Some blockchains and protocols that have implemented hash functions in ZKPs include Zcash, StarkWare, and Ethereum (zk-Rollups).


Pingback: Blockchain Technology: A Comprehensive Guide - coinrin.com